
DDoS protection at a glance
Cyber attacks such as Distributed Denial of Service (DDoS) attacks threaten companies with a revenue loss, as well as reputational and productivity losses. Still, many companies always leave their online systems unprotected. The market offers many DDoS protection products, some of them also suitable for SME budgets. You have to keep track of which technology and solution is right for your purposes.
In its latest State of the Internet Security report, Akamai, a leading provider of DDoS solutions and cloud security, sees a 14% increase in DDoS attacks. This refers to the fourth quarter of 2017 compared to the same period last year. In addition, the report notes that DDoS attacks today are still more often addressing the application layer ( Layer 7 ) than the network or transport layer ( Layer 3 and 4). Here, the increase was 22 percent compared to the same period last year.
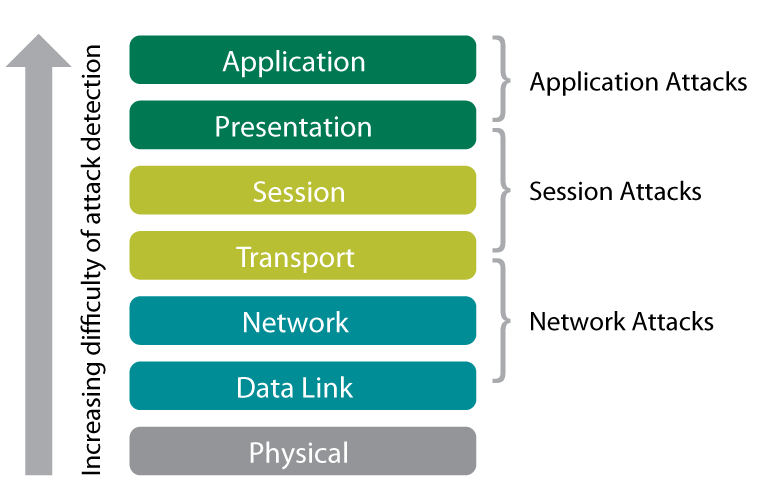
In contrast to the classic DDoS attack, this is not about overloading systems and thus influencing their availability. Also, vulnerabilities of an application (databases, mail programs, etc.) are sought and exploited to manipulate or steal data. In addition, attackers like to combine multiple attack vectors to avoid defensive methods and do as much damage as possible. A professional DDoS protection solution should, therefore, be on the agenda of every IT security officer.
Overview of DDoS mitigation
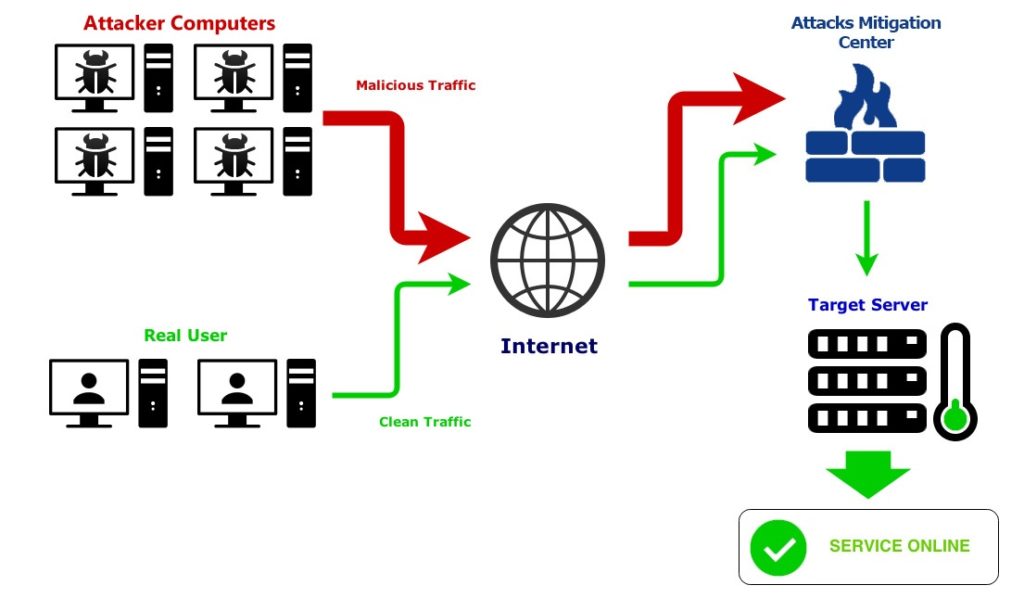
From free basic protection in the provider’s data center to dedicated hardware, to various cloud-based solutions, the vast majority of DDoS mitigation solutions available on the market can be broken down into a handful of technologies. Further, the providers can be differentiated in terms of quality (for example, the offered “time to mitigate”, ie the reaction time before the defense begins) and the price.
Basic protection in the data center
If you operate your infrastructure externally with a hosting or cloud provider, you can assume that the provider has set up basic protection in your own data center. Some providers also promote this as a free DDoS protection for customers. However, the primary goal is to secure your own networks. Nonetheless, basic protection ensures that one customer’s systems remain accessible while attacks on other customers occur on the same network. All types of attacks are quickly detected and appropriate countermeasures are taken. However, the accessibility of an attack against their own systems is not guaranteed by this solution. In addition, downtime due to DDoS attacks is typically excluded by the Service Level Agreements (SLA).
DNS forwarding or CDN-based solutions
Most content delivery network ( CDN ) operators also use their globally distributed infrastructure for effective DDoS protection solutions. A CDN is typically designed to streamline delivery of content to all parts of the world. For this purpose, the provider operates numerous CDN nodes, where a filtering of the incoming traffic can take place on attack patterns. These solutions are also called DNS Forwarding Solutions: The DNS entries of the environment to be protected are adjusted so that the traffic first passes through the mitigation infrastructure. Attacks are already blocked at the edge of the network before they reach the customer’s systems. These solutions protect a website or webshop from all types of DDoS attacks based on TCP and TCP-HTTP. In addition, it is possible to integrate a WAF (Web Application Firewall) and prevent attacks on web applications.
BGP routing or DDoS Scrubbing Center
Comprehensive protection of the entire hosted infrastructure – e-commerce store or website, VPN, FTP, mail servers, databases, etc. – is provided by BGP-based products. They work with a permanent routing of incoming traffic through the Border Gateway Protocol on external “scrubbing” (Scrubbing Center) of the respective security provider. All traffic to the customer’s environment is filtered there and then continued via a secure line to the target system. The hosting infrastructure is protected against most types of DDoS attacks based on TCP, TCP-HTTP, UDP, and ICMP. Above all, scrubbing solutions are able to ward off large volumetric attacks and detect multivector attacks more quickly.
Special solution for smaller projects
Today, especially small and medium-sized companies should consistently deal with an effective DDoS defense. At least when most of their business depends on accessibility via the Internet. Because the daily practice of a hosting and cloud provider shows that SMEs are increasingly becoming the target of cyber attacks. The reason: They do not have their own protection solution for budget reasons and are therefore a grateful victim of extortionate DDoS attacks. However, especially for smaller and mid-sized projects, a DDoS protection solution based on the economic cloud principle has recently been on the market. This means that the underlying infrastructure is shared by multiple customers, reducing the cost to the individual.FTP server).
Help with the selection
According to Radware’s 2017 Executive Application & Network Security Survey , 40 percent of medium and large enterprises rely on their service provider for DDoS protection. In addition to a neutral advice, this also offers the appropriate products from different manufacturers from a single source, which reduces the effort for companies.
Contact Bleuwire™ to learn about how to prevent denial of service attacks and Web Application Firewall protection for small business – how we can help your business.





