It is difficult to manage access to enterprise networks. Most people are working remotely from their homes now. Also, they are using personal devices for accessing corporate data and applications. Thus, companies must implement better security controls. These security controls will help companies in protecting their data. Multi-Factor Authentication is one of the best ways to protect your data. It will ensure that only authorized users can access enterprise networks.
Definition of Multi-Factor Authentication:
The biggest challenge that organizations are facing is to protect their user accounts from unauthorized access. Password protection is not very effective as passwords can get stolen. Sometimes hackers can use a simple brute force attack for hacking into your employee’s account. Thus, you can’t rely only on passwords. If you are relying on passwords only, then it will act as a single POF in your network.
If your employee’s account password gets compromised, then hackers can get access to your sensitive applications and data. Cybersecurity experts are promoting various password practices. You can create strong passwords by alphanumeric characters and symbols in your password. However, even these strong passwords can get leaked.
MFA will act as an additional security layer. First, your users need to provide the correct password. However, they can’t access your files by just providing the correct password. They also need to produce additional credentials for accessing their accounts. This will ensure that intruder can’t access your employees account after stealing their passwords. It is almost impossible to steal OTP codes from your employee’s phone. Thus, multi-factor authentication is very important for your network.
According to a report by Microsoft, you can block more than 99.9% of account hacking attempts by using multi-factor authentication. Google has also reported similar findings. The best thing about multi-factor authentication is that it can stop acts like phishing and brute-force. Thus, hackers can’t use automated python bots for hacking your network. They need to use better techniques for cracking your MFA software. However, most attackers don’t have time to crack MFA software. They need to invest a lot of resources and time into cracking MFA software.
How MFA works?
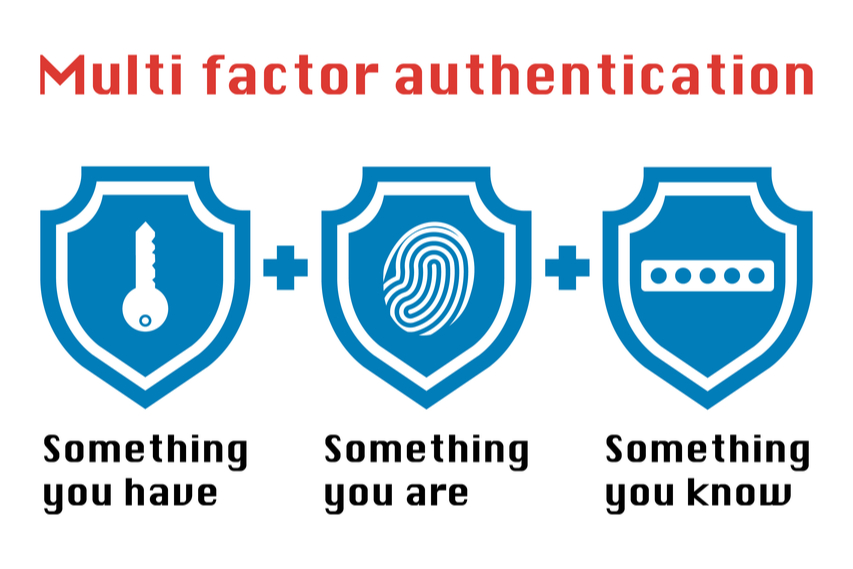
MFA security works on a simple idea. Your users can provide three forms of credentials for proving authenticity. They should prove that they are your employees. The three basic forms of credentials are:
- Something you are: Your users can use unique identifiers for proving that they are real. It is difficult to copy these things. For example, you can ask for a retina pattern or fingerprint.
- Something you have: Your employees might have access to a unique object like an access card or keycode. They can use it for proving their credentials.
- Something you know: Your users can also provide information that is only known to them. For example, they can tell the password or OTP.
Your users need to present two forms of credentials. They can’t access your systems until they present two different forms of credentials. Most enterprises are now actually using this system. However, you can also use it for securing your physical security systems. For example, data centers are using MFA security for protecting their server and assets.
Two-Factor Authentication:
The most common form of MFA that companies are using is two-factor authentication. It is also known as two-step security. The best thing about two-factor authentication is that it is easy to implement when compared to other solutions. You can combine your user’s password with an OTP. Your server can send a one-time password or uniquely generated keycode to your user’s smartphone. Thus, you can combine something you have with something you know. Your user will first enter their password. However, they still can’t access your system and files. Your MFA software will first create a time-sensitive OTP and send it to their smartphone. They need to enter the code before it expires. In general cases, this code will expire in a few minutes. This will ensure that attackers can’t use the same code in the future.
This is the simplest form of a multi-factor authentication system. However, it is very effective against attacks like brute force attacks. Attackers can’t use simple attacks like brute-force for hacking into your network. It is not easy to bypass or crack the two-factor authentication network. First, an attacker needs to find the user’s password by using some software. After that, they need to steal the OTP from their device. The only way to do this is by hacking your user smartphone. However, it is very difficult to hack a smartphone. Thus, attackers will generally move on to a simple target. They will generally look for companies that are only using a password system.
The best thing about this security system is that it is very simple to implement. Also, it is unobtrusive for your employees. Your employees might think that they are wasting their seconds entering a key code. However, it can protect your company from data breaches.
Biometric Authentication:
Biometric scanning is an excellent way to protect your office and data centers. There are many ways to collect biometric data. You can collect data from scanning devices, touch sensors, and cameras. Most people are using biometric authentication for confirming purchases on app stores. They are using biometric data for accessing mobile banking dashboards.
Biometric authentication is basically using the “something you are” aspect. It will turn the user’s biological features into credentials. Only your users will have access to these unique credentials. Thus, hackers can’t access your user’s account even after stealing their passwords. It is easy to steal passwords and sometimes even physical credentials can get misplaced. However, it is almost impossible to duplicate biometric information. The best thing about biometric data is that your users don’t need to obtain any keycode. It is one of the quickest and easiest methods to increase your security.
Conclusion
You can use multi-factor authentication for increasing your network security. It will ensure that only your employees can access your network. However, it is difficult to implement MFA controls. Thus, you should consider working with an MSP like Bleuwire. Experienced MSPs like Bleuwire will help you in implementing security access controls. They will help you in implementing the best security solutions. If you need more tips regarding network security, then you can contact Bleuwire.
Contact us today to learn about Bleuwire™ services and solutions in how we can help your business.





